Introduction – Office 365 Security
Customers often migrate their email to MS Office 365 without considering the change in security landscape. Migrating to Office 365 offers the convenience of a cloud solution, but we recommend focusing on cloud security at the same time.
Security aspects of MS Office 365 are wide ranging, but this blog post aims to introduce some of the basic concepts, based around risk.
Everyone’s appetite for risk is different, which makes it a useful starting place for securing Office 365. For example, a school’s use of Office 365 may have lesser security risks than a military organisation. An extreme example maybe, but it helps to understand the point.
I like to use sliders to represent Office 365 security – you cannot move one slider without causing the others to move. This provides a good place to start when looking at Office 365 and security.
Slider One – Just Migrated to Office 365
The following slider picture is typical of most organisations after they started using Office 365 for their email service (Day 1).
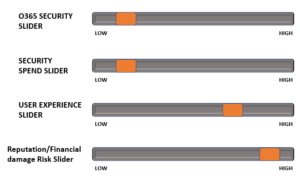
You can see that user experience is very high with the adoption of the Office 365 cloud service, allowing access from any browser to Office 365. There has been little spend on IT security. Consequently there is a higher risk of reputation/financial risk via malicious actions – resulting from compromised user credentials. This is due to the login access points being more widely available.
Slider Two – Future O365 State
The next slider shows the desired state after increasing security measures to reduce the reputation/financial risk. This is achieved by reducing the risk of malicious actions taking place. To mitigate these risks involves the other sliders moving!
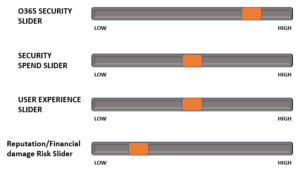
This can be done via some simple measures, such as:
- Conditional Multi-Factor Authentication for all browser sign-ins from non-trusted devices, and/or from non-trusted network locations
- Configure Outlook Web App policy to prevent files from being downloaded
- Disable basic authentication
There are more measures, but these are some simple ones to think about.
Example O365 Security Use Cases
This section presents some use cases to consider when assessing your risk appetite.
O365 Security Use Case #1
Contuso user uses a Windows PC in an internet café to access Office 365 services via a browser. They logout when finished and walk away. A key logger was on the machine, and their credentials have been compromised by a malicious actor.
Impact
The 365 credentials are used to login as the Contuso user on a browser. Data is accessed, email is accessed, a new email rule is created to redirect all inbound mail to an external mailbox. Payroll are emailed to change the bank account for salary. A malicious email is then sent out to customers.
Mitigation
Enforce 2FA for any O365 browser sign-on from a non-trusted network.
O365 Security Use Case #2
Contuso user uses a Windows PC in an internet café to access Office 365 services via a browser. They access Outlook Web App and open an Excel spreadsheet attached to an email – they are asked if they want to Save it locally. They do so, and use local Excel to view the spreadsheet. They then logout of O365 on the browser, and walk away.
Impact
A malicious actor finds the Excel file via the Recent files feature, and opens it. They use the information to damage the Contuso brand.
Mitigation
Change the default Outlook Web App policy to disable Direct File Access, and to only allow documents to be viewed in the preview pane. No local save is allowed.
Disallow document repository O365 services such as Sharepoint and OneDrive from being accessed from a non-trusted desktop
O365 Security Use Case #3
A Contuso user is using their personal smartphone for Outlook access via the Outlook Mobile App. The phone does not belong to any O365 MDM policy, and has no PIN lock set. The phone is stolen, and the user informs Contuso IT department. IT disables his account and mailbox.
Impact
Contuso email data is available for the malicious actor to access.
Mitigation
Only allow Outlook Mobile App to connect to Contuso O365 if the user accepts the enrollment of the device into the Contuso MDM policy. This then allows for a remote wipe of the device to take place.
Conclusion
When planning to migrate your email to MS Office 365, please give the security landscape serious consideration, and make any initial security changes as part of the email migration plan.
We can provide consulting to produce an Office 365 Security Risk Paper for your company, that will get you started with some basic configurations and policies. Get in touch for a quote.